ITC == Introduction To Cryptography
Some …
ITC == Introduction To Cryptography
Some notes about the Homework #2
1. Generator
(a) Generator
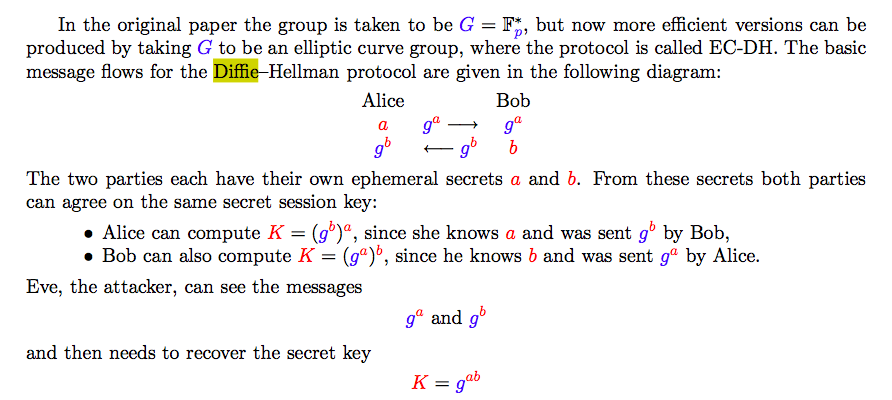
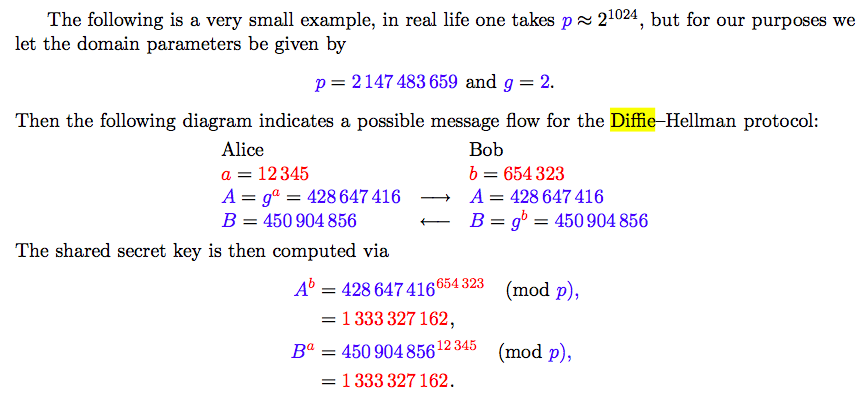
(b) Diffie-Hellman Key Exange Protocol
- allows two parties to agree a secret key over an insecure channel without having met before.
- Its security is based on the discrete logarithm problem in a finite abelian group G.
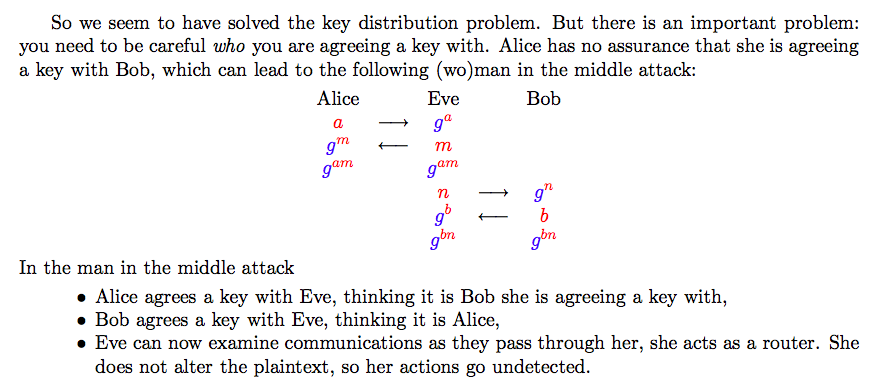
(c) Man-in-the-Middle attack
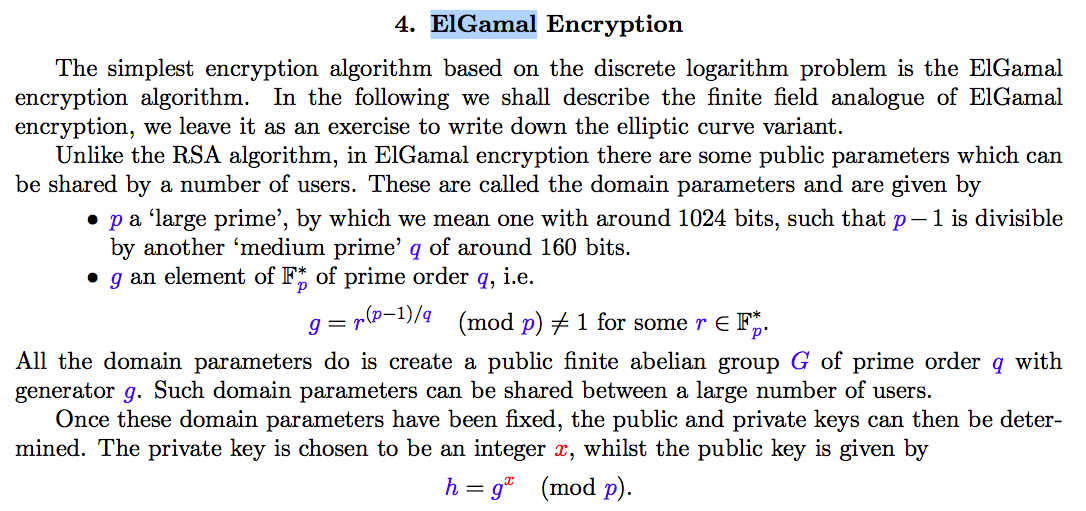
(d) ElGamal cryptosystem
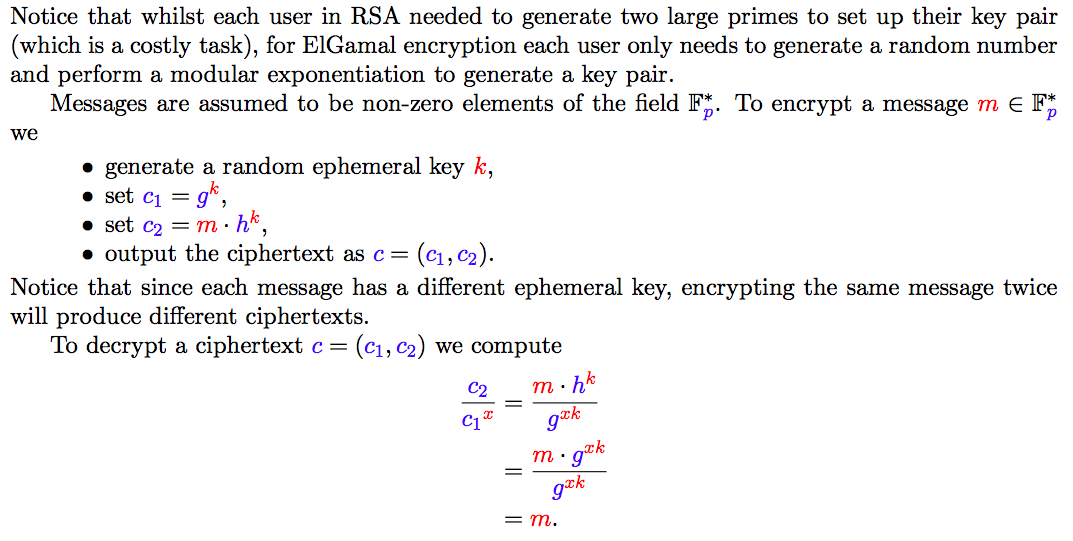

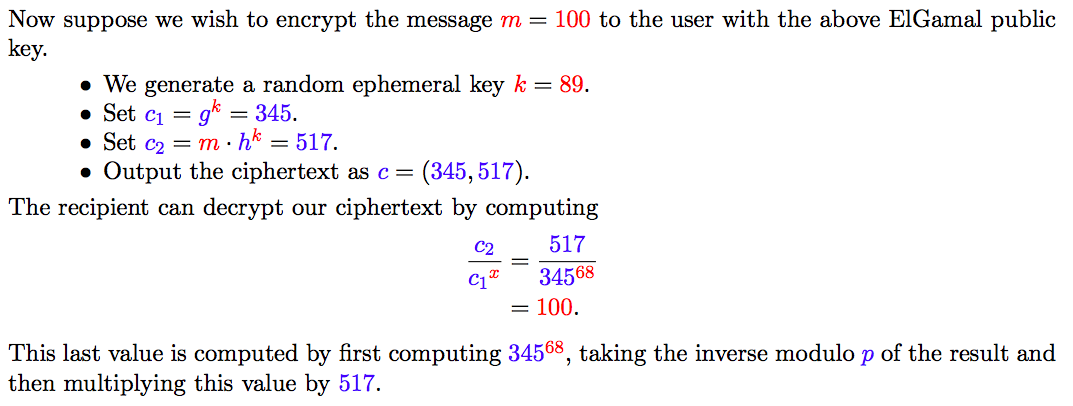
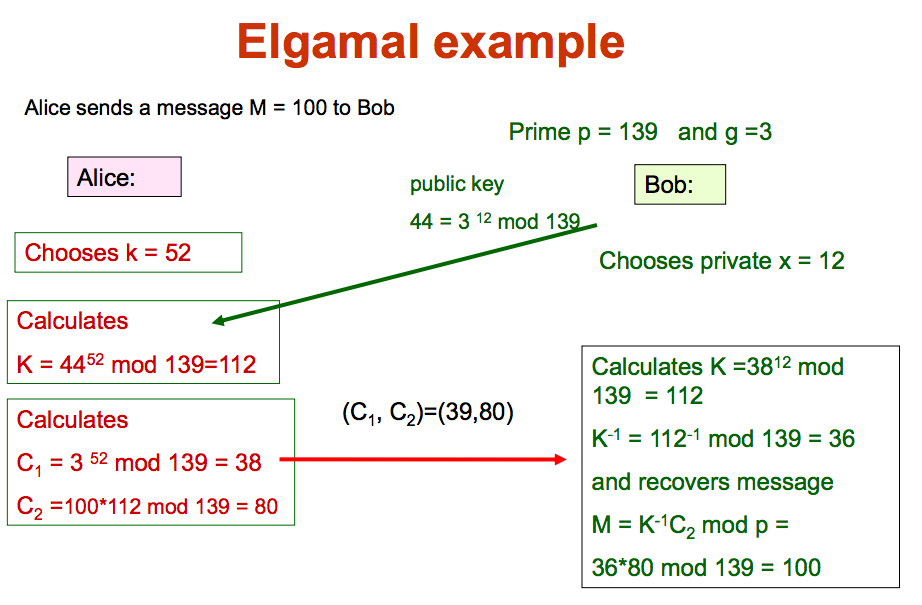
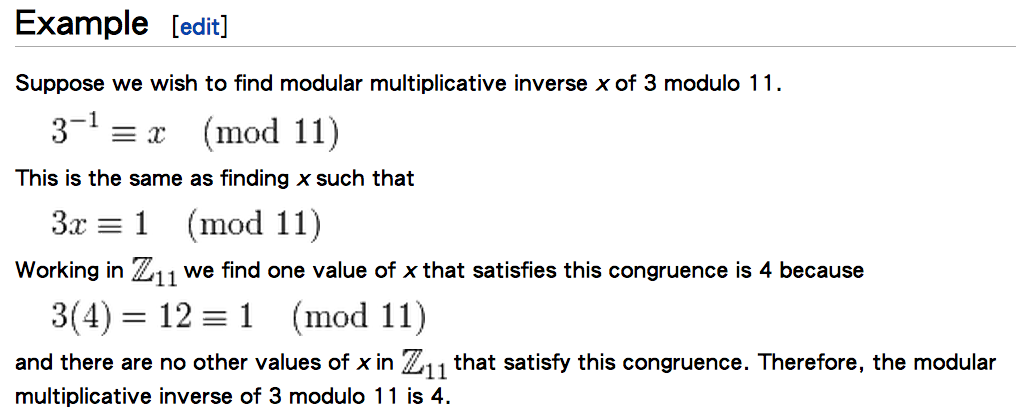
Modular multiplicative inverse
2. Euler’s Theorem is the extension of Fermat’s Theorem.
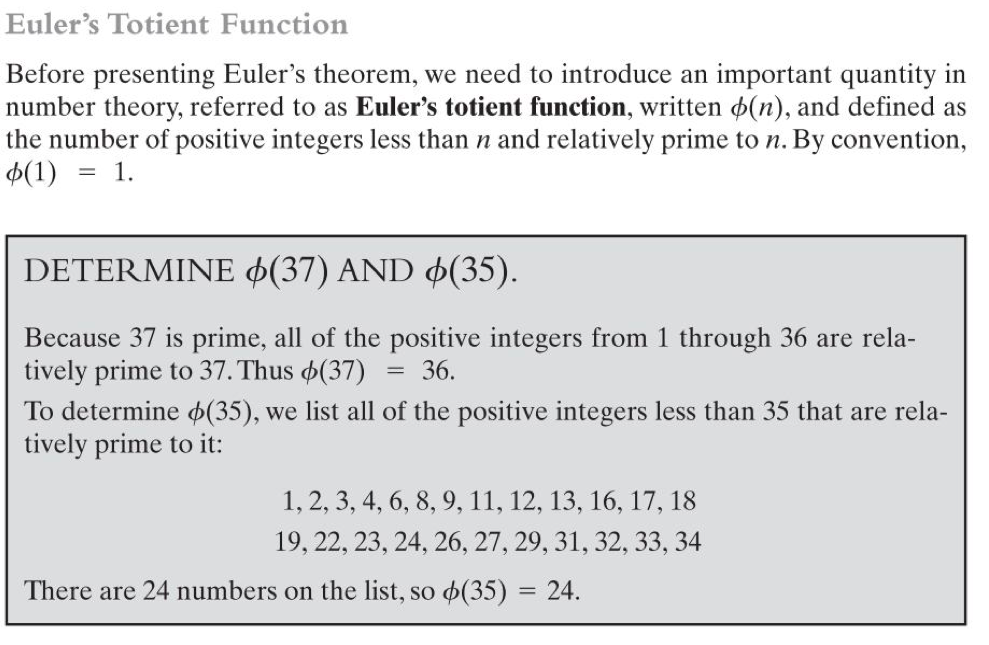
(a) Euler’s totient function


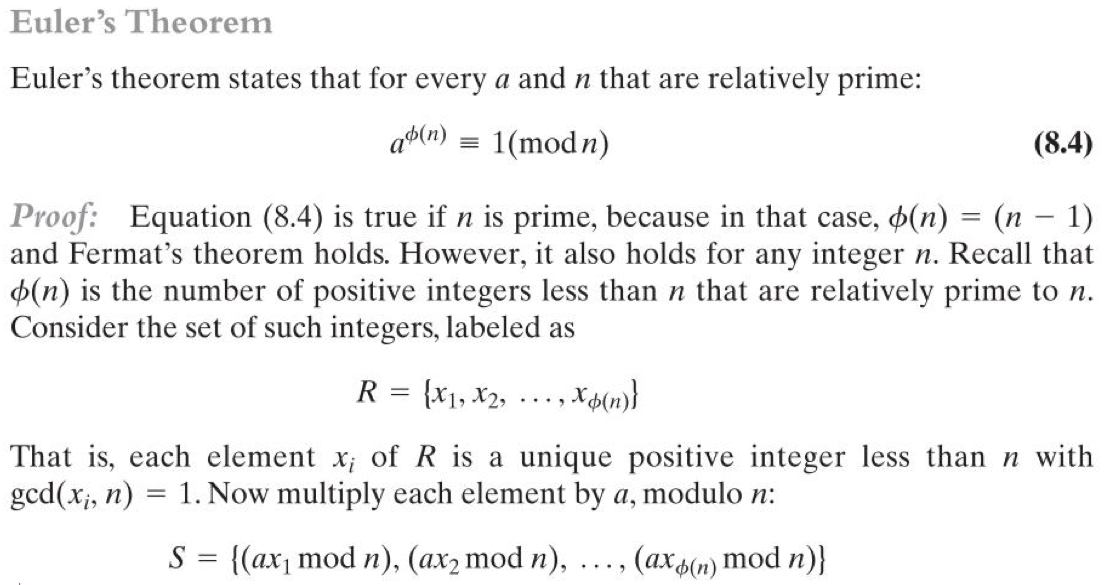
(b) Euler’s Theorem
(c) the last 3 digits of 8^803

8^{803} \mod 1000 \equiv 8 \times 64^{400+1} \mod 1000 \equiv 8 \times 64 \equiv 512
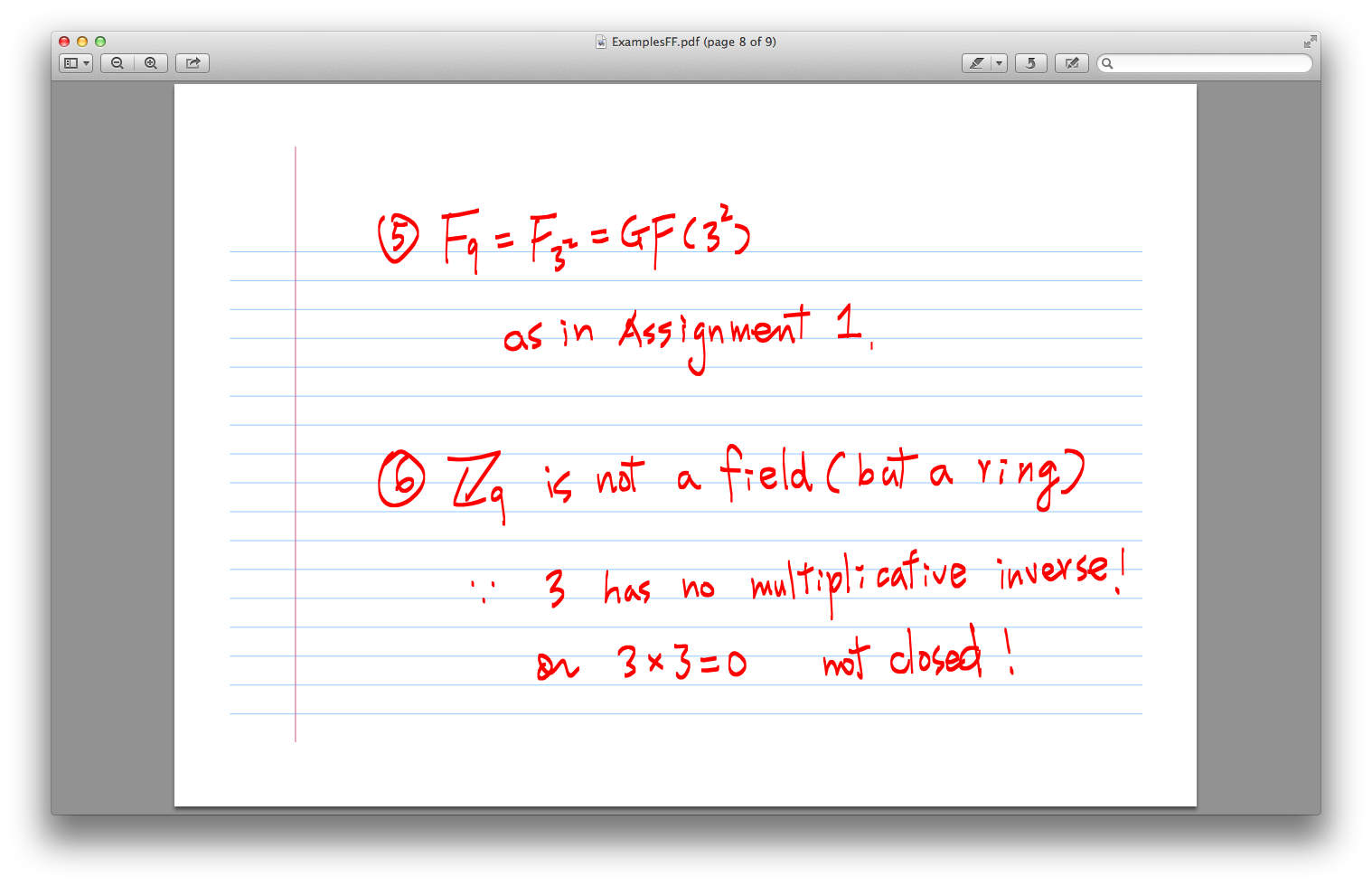
3.
multiplicative inverse
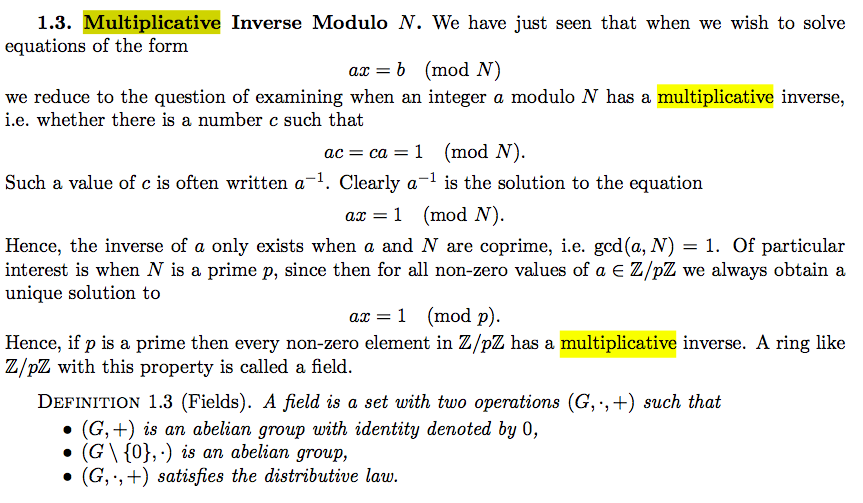
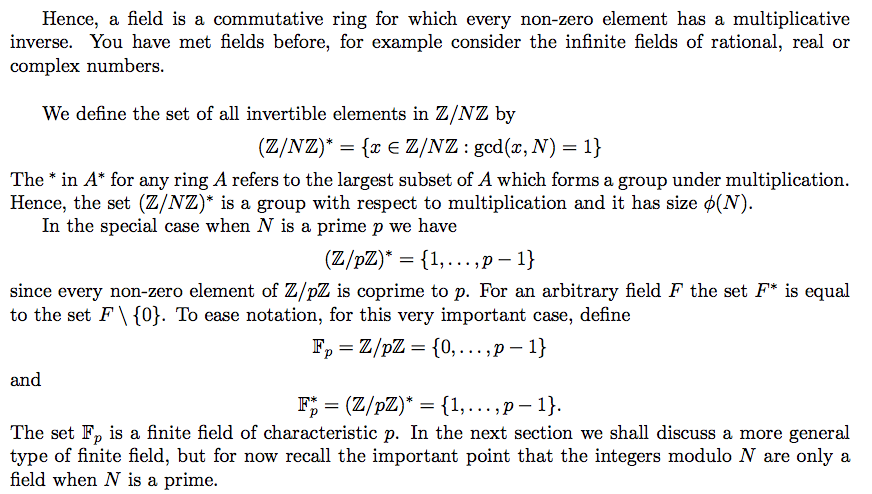
finite field

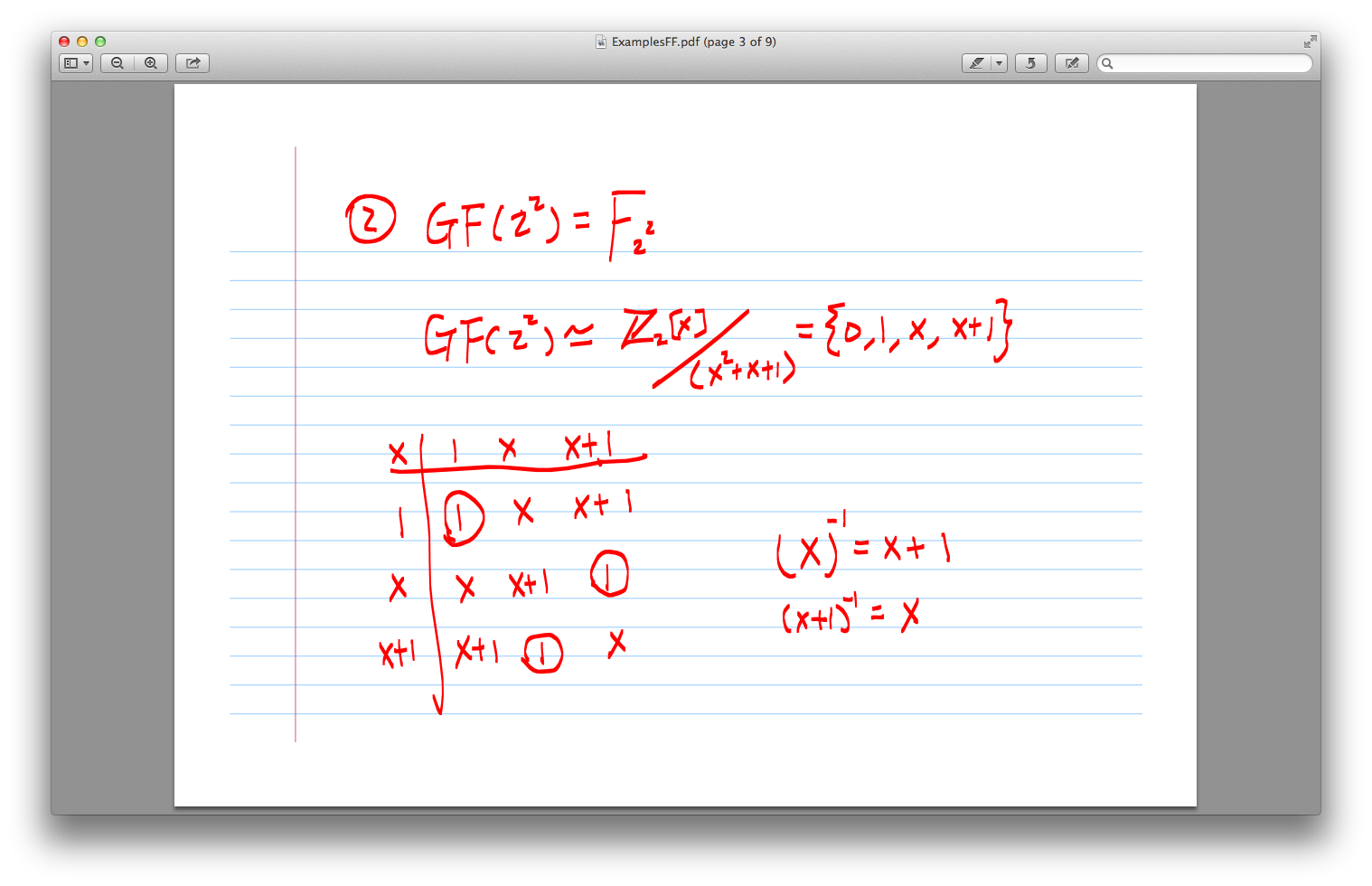
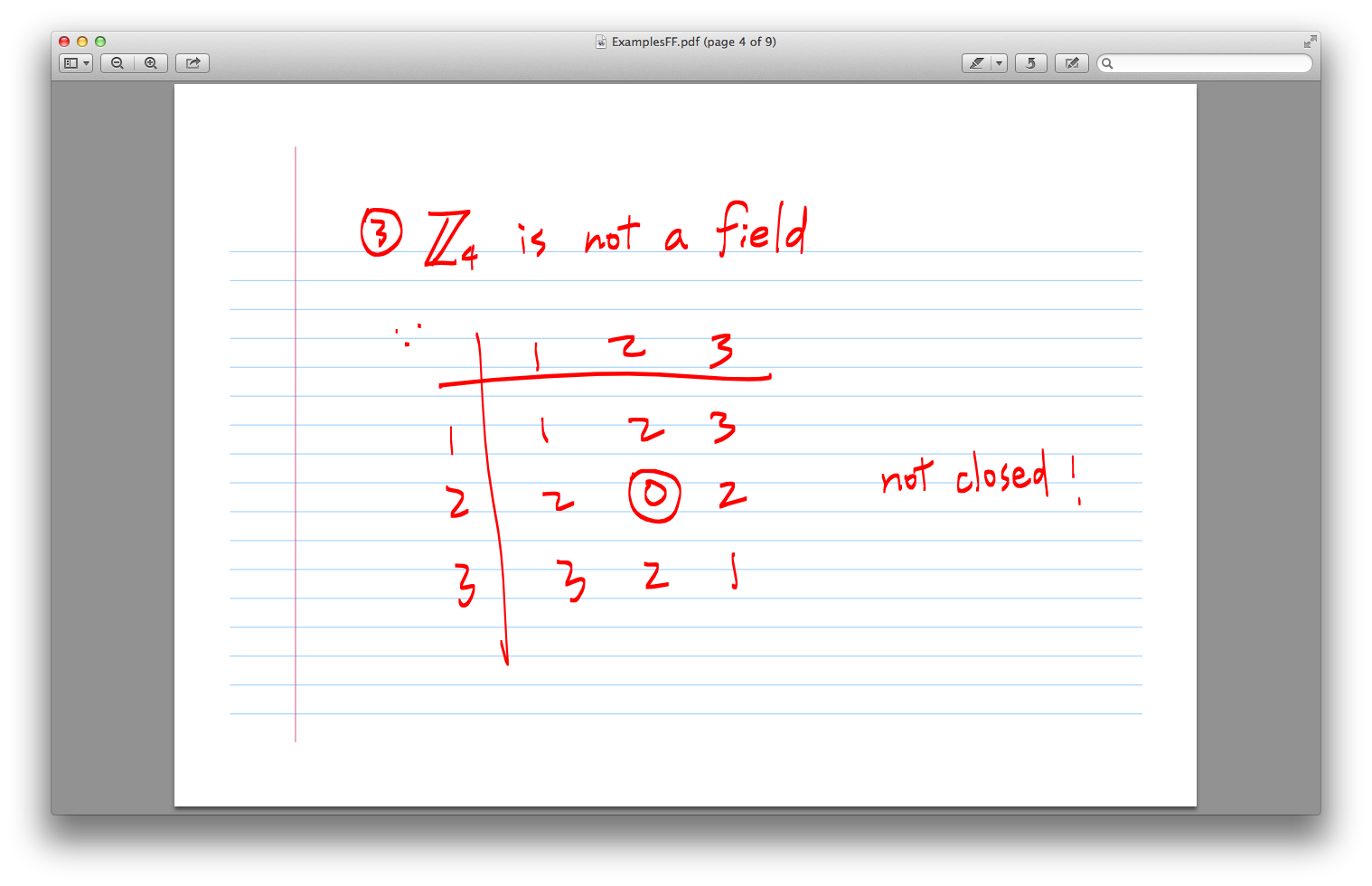
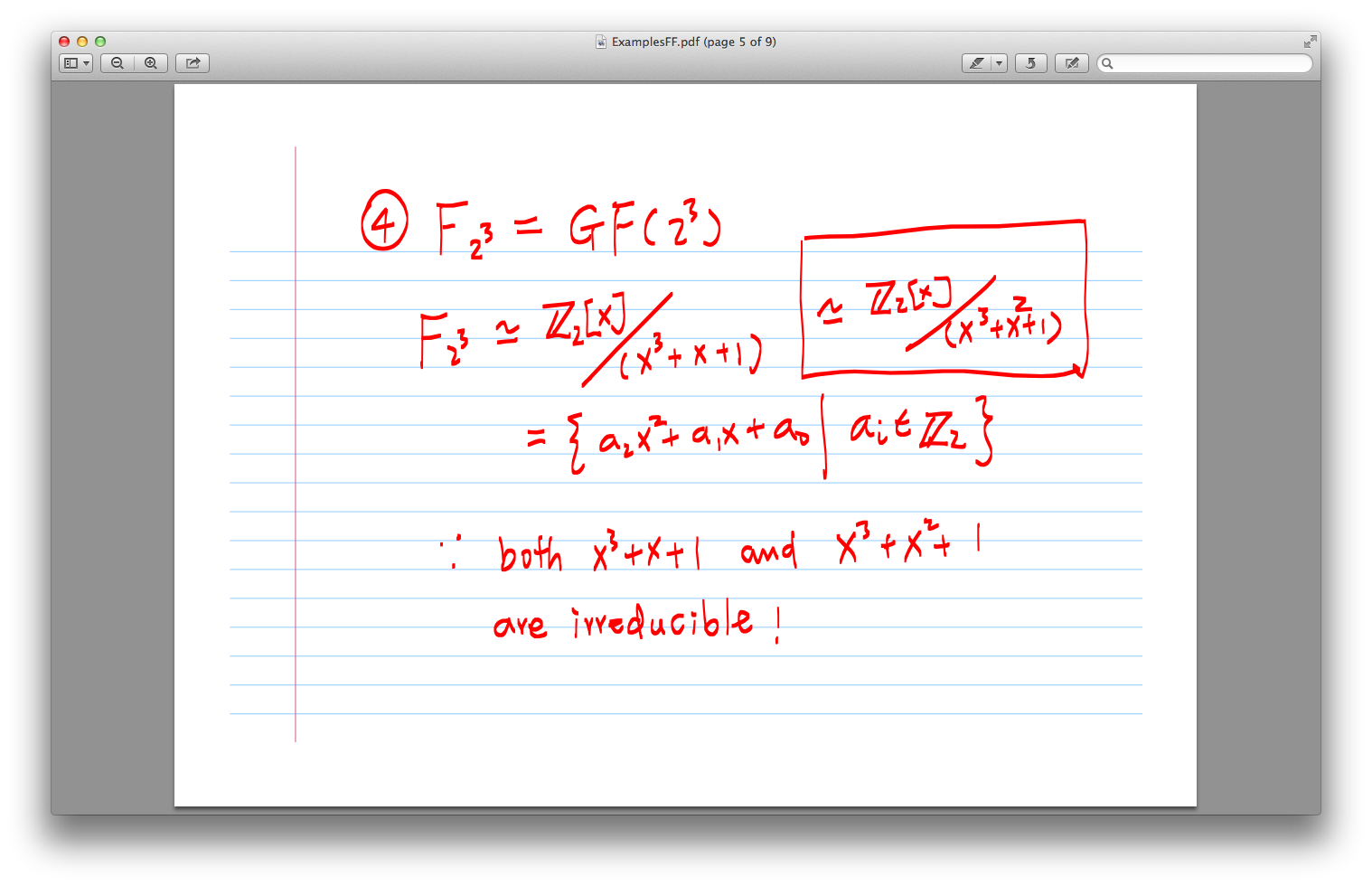
4. RSA
p, q, e, n, d
use Extended Euclidean algorithm
5. system of equations
Still don't get it...
Share
Donation
如果覺得這篇文章對你有幫助, 除了留言讓我知道外, 或許也可以考慮請我喝杯咖啡, 不論金額多寡我都會非常感激且能鼓勵我繼續寫出對你有幫助的文章。
If this blog post happens to be helpful to you, besides of leaving a reply, you may consider buy me a cup of coffee to support me. It would help me write more articles helpful to you in the future and I would really appreciate it.
Related Posts
- ITC week10 - Key Management and Distribution
- ITC week8 - LFSR-based Stream Cipher
- ITC - week7
- ITC week9 - Hash
- 資訊工程研討 - 台灣資安防護及技術發展現況